In December 2022, KrebsOnSecurity broke the information {that a} cybercriminal utilizing the deal with “USDoD” had infiltrated the FBI‘s vetted info sharing community InfraGard, and was promoting the contact info for all 80,000 members. The FBI responded by reverifying InfraGard members and by seizing the cybercrime discussion board the place the info was being offered. However on Sept. 11, 2023, USDoD resurfaced after a prolonged absence to leak delicate worker knowledge stolen from the aerospace large Airbus, whereas promising to go to the identical therapy on high U.S. protection contractors.

USDoD’s avatar was the seal of the U.S. Division of Protection. Now it’s a captivating kitten.
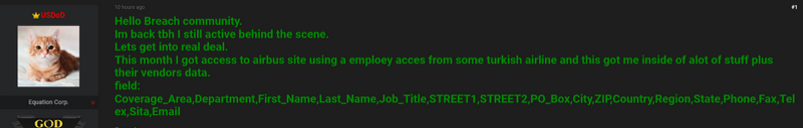
In a publish on the English language cybercrime discussion board BreachForums, USDoD leaked info on roughly 3,200 Airbus distributors, together with names, addresses, telephone numbers, and e-mail addresses. USDoD claimed they grabbed the info by utilizing passwords stolen from a Turkish airline worker who had third-party entry to Airbus’ methods.
USDoD didn’t say why they determined to leak the info on the twenty second anniversary of the 9/11 assaults, however there was undoubtedly an plane theme to the message that accompanied the leak, which concluded with the phrases, “Lockheed martin, Raytheon and all the protection contractos [sic], I’m coming for you [expletive].”
Airbus has apparently confirmed the cybercriminal’s account to the risk intelligence agency Hudson Rock, which decided that the Airbus credentials have been stolen after a Turkish airline worker contaminated their pc with a prevalent and highly effective info-stealing trojan referred to as RedLine.
Data-stealers like RedLine usually are deployed by way of opportunistic e-mail malware campaigns, and by secretly bundling the trojans with cracked variations of common software program titles made obtainable on-line. Credentials stolen by info-stealers typically find yourself on the market on cybercrime outlets that peddle purloined passwords and authentication cookies (these logs additionally typically present up within the malware scanning service VirusTotal).
Hudson Rock said it recovered the log information created by a RedLine an infection on the Turkish airline worker’s system, and located the worker probably contaminated their machine after downloading pirated and secretly backdoored software program for Microsoft Home windows.
Hudson Rock says info-stealer infections from RedLine and a bunch of comparable trojans have surged in recent times, and that they continue to be “a main preliminary assault vector utilized by risk actors to infiltrate organizations and execute cyberattacks, together with ransomware, knowledge breaches, account overtakes, and company espionage.”
The prevalence of RedLine and different info-stealers signifies that a fantastic many consequential safety breaches start with cybercriminals abusing stolen worker credentials. On this state of affairs, the attacker briefly assumes the id and on-line privileges assigned to a hacked worker, and the onus is on the employer to inform the distinction.
Along with snarfing any passwords saved on or transmitted via an contaminated system, info-stealers additionally siphon authentication cookies or tokens that permit one to stay signed-in to on-line companies for lengthy intervals of time with out having to resupply one’s password and multi-factor authentication code. By stealing these tokens, attackers can typically reuse them in their very own internet browser, and bypass any authentication usually required for that account.
Microsoft Corp. this week acknowledged {that a} China-backed hacking group was in a position to steal one of many keys to its e-mail kingdom that granted near-unfettered entry to U.S. authorities inboxes. Microsoft’s detailed post-mortem cum mea culpa defined {that a} secret signing key was stolen from an worker in an unfortunate sequence of unlucky occasions, and due to TechCrunch we now know that the perpetrator as soon as once more was “token-stealing malware” on the worker’s system.
In April 2023, the FBI seized Genesis Market, a bustling, totally automated cybercrime retailer that was constantly restocked with freshly hacked passwords and authentication tokens stolen by a community of contractors who deployed RedLine and different info-stealer malware.
In March 2023, the FBI arrested and charged the alleged administrator of BreachForums (aka Breached), the identical cybercrime neighborhood the place USDoD leaked the Airbus knowledge. In June 2023, the FBI seized the BreachForums domain name, however the discussion board has since migrated to a brand new area.
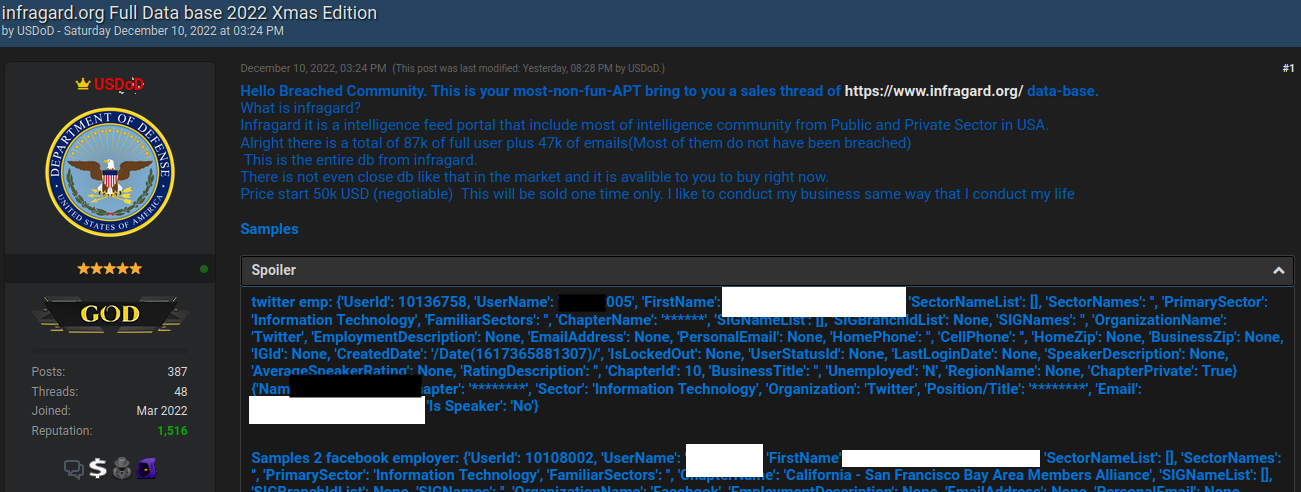
USDoD’s InfraGard gross sales thread on Breached.
Unsolicited e-mail continues to be an enormous vector for info-stealing malware, however currently the crooks behind these schemes have been gaming the various search engines in order that their malicious websites impersonating common software program distributors truly seem earlier than the legit vendor’s web site. So take particular care when downloading software program to make sure that you’re in actual fact getting this system from the unique, legit supply at any time when potential.
Additionally, until you actually know what you’re doing, please don’t obtain and set up pirated software program. Certain, the cracked program may do precisely what you anticipate it to do, however the chances are high good that it is usually laced with one thing nasty. And when your entire passwords are stolen and your vital accounts have been hijacked or offered, you’ll want you had merely paid for the true factor.